
Cognitive training apps continue to gain traction among older adults seeking to maintain or improve cognitive function. While many available tools show promise, recent evaluations highlight an important reality: current apps designed for older adults with mild cognitive impairment offer moderate overall quality and significant variability in effectiveness, usability, and evidence-based support. Understanding where these…
Read more
The rapid expansion of artificial intelligence is driving an unprecedented surge in global demand for computer memory, causing steep price hikes for RAM, SSDs, and other storage components. Major AI developers—including OpenAI, Google, Microsoft, and Amazon—are buying massive quantities of high-end memory for their data centers, often outbidding consumer manufacturers. As a result, the cost…
Read more
The U.S. Department of Energy and Advanced Micro Devices (AMD) have announced a $1 billion partnership to build two next-generation supercomputers, named Lux and Discovery, at Oak Ridge National Laboratory in Tennessee. The systems are designed to accelerate research in nuclear energy, national security, and cancer treatment. Energy Secretary Chris Wright said the new systems…
Read more
Google is phasing out reCAPTCHA Classic and moving all users to reCAPTCHA Enterprise under the Google Cloud platform by the end of 2025. Why the Change? Google is making this update to strengthen online security as internet threats evolve. The familiar checkbox or image puzzle asking, “Are you a robot?” is part of Google’s reCAPTCHA…
Read more
Creative Programs & Systems (CPS) Makes IT Easy! If your computers aren’t making your life easier, it’s time to reach out for help. At CPS, we solve complex technology challenges and streamline processes with proven strategies and dedicated support tailored to your business needs. IT Support Made Simple 1. Assess -We start by learning your…
Read more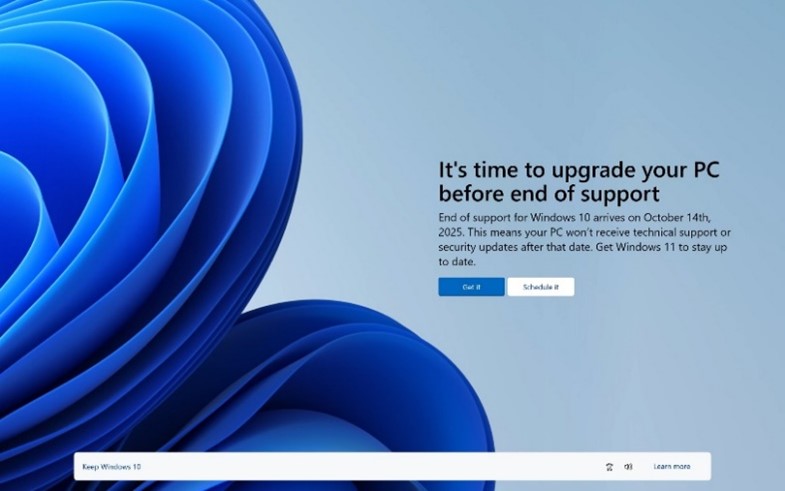
Microsoft will end support for Windows 10 on October 14, 2025. Additionally, Windows 11 has limited compatibility with older hardware, meaning many computers will need to be replaced rather than upgraded. Running an unsupported operating system isn’t just inconvenient—it’s a serious security risk. It can also cause you to fall out of compliance with critical…
Read more